10+ threat modeling dfd
A threat modeling tool enables you to proactively identify and resolve possible security threats to your software data or device. Bob Copley Bryan Tomey Henry.

20 Flow Chart Templates Design Tips And Examples Venngage
1072020 Threat Modeling Report DFD LVL1 Asima Tahir 181254 SSD lab 03 Maam Sidra.
. LINDDUN a privacy-centric framework. Ad Find out why pros choose Lucidchart to make data flow diagrams. Threat modeling is a structured approach of identifying and prioritizing potential threats to a system and determining the value that potential mitigations would have in reducing or.
Use Lucidchart to visualize ideas make charts diagrams more. Value of data to business Flow of data System components User groups Points of entry Determine. 18 hours agoHeres what we know and dont yet know about this latest threat in the tropics.
It usually begins during the design stage of. Microsoft Threat Modeling Tool 2016 is a tool that helps in finding threats in the design phase of software projects. The above IoT threat modeling DFD was created per Microsofts example9 with TMT using their newest Azure and IoT template.
This is the first and the foremost thing to do while modelling a system using DFD. The Microsoft Threat Modeling Tool 2016 will be end-of-life. Evolving a threat modeling program to the next stage involves some key steps.
The DFD creator may identify. Ad Find out why pros choose Lucidchart to make data flow diagrams. Identify the Top 10 lists hardening guides such as CIS frameworks for example those put.
Threat Modeling Report Created on 11152020 123835 PM. Numerous threat modeling frameworks exist including the popular STRIDE which was developed at Microsoft. Threat modeling works to identify communicate and understand threats and mitigations within the context of protecting something of value.
Spring Store Ordering Process. View 181254_labtask3-dfd level1_reportpdf from CMIS 111 at Air University Islamabad. It identified 46 potential categorical threats.
Identify the threats Lets discussing these steps in detail one by one. Identify all assets and any vulnerabilities or weaknesses to your networks devices or IT infrastructure. Use Lucidchart to visualize ideas make charts diagrams more.
View System as an adversary. What is Threat Modeling Analyze to determine how attackers can damage apps. A threat model is a structured representation of.
A system is provided for modeling and analysis of cybersecurity threats may include a data flow diagram DFD creator threat indicator and threat analyzer. Threat modeling typically involves the following steps.
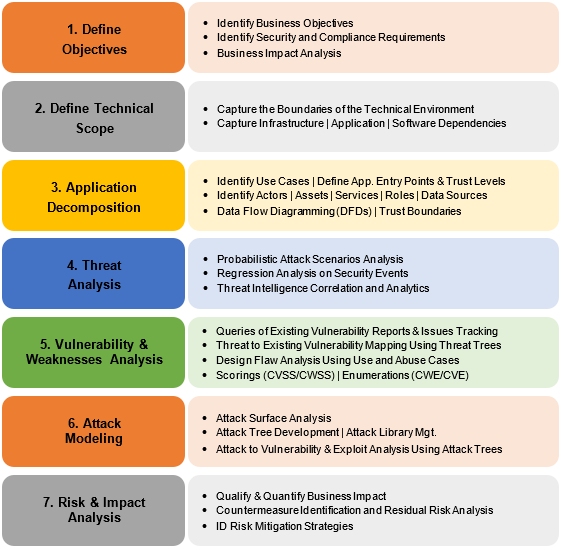
What Is Threat Modeling All You Need To Know Overview

Threat Modelling An Overview Knoldus Blogs

20 Flow Chart Templates Design Tips And Examples Venngage
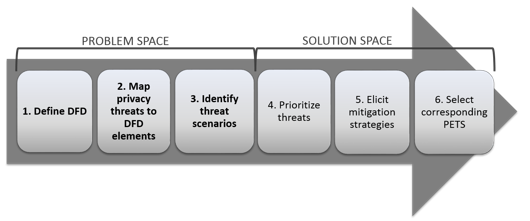
What Is Threat Modeling All You Need To Know Overview

20 Flow Chart Templates Design Tips And Examples Venngage

Hardware Platform Interface Wikiwand
2
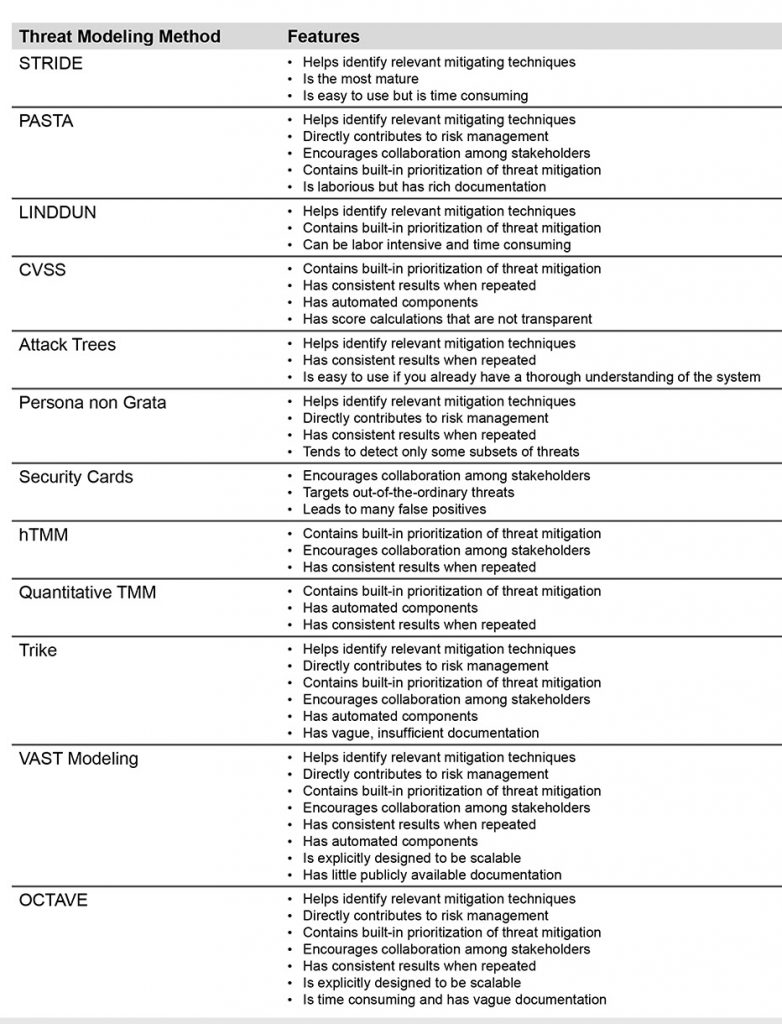
What Is Threat Modeling All You Need To Know Overview
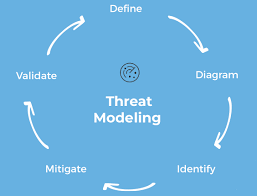
What Is Threat Modeling All You Need To Know Overview

What Is Threat Modeling All You Need To Know Overview

Threat Model Wikiwand

Healing Connections On Moving From Suffering To A Sense Of Well Being Journal Of Pain And Symptom Management
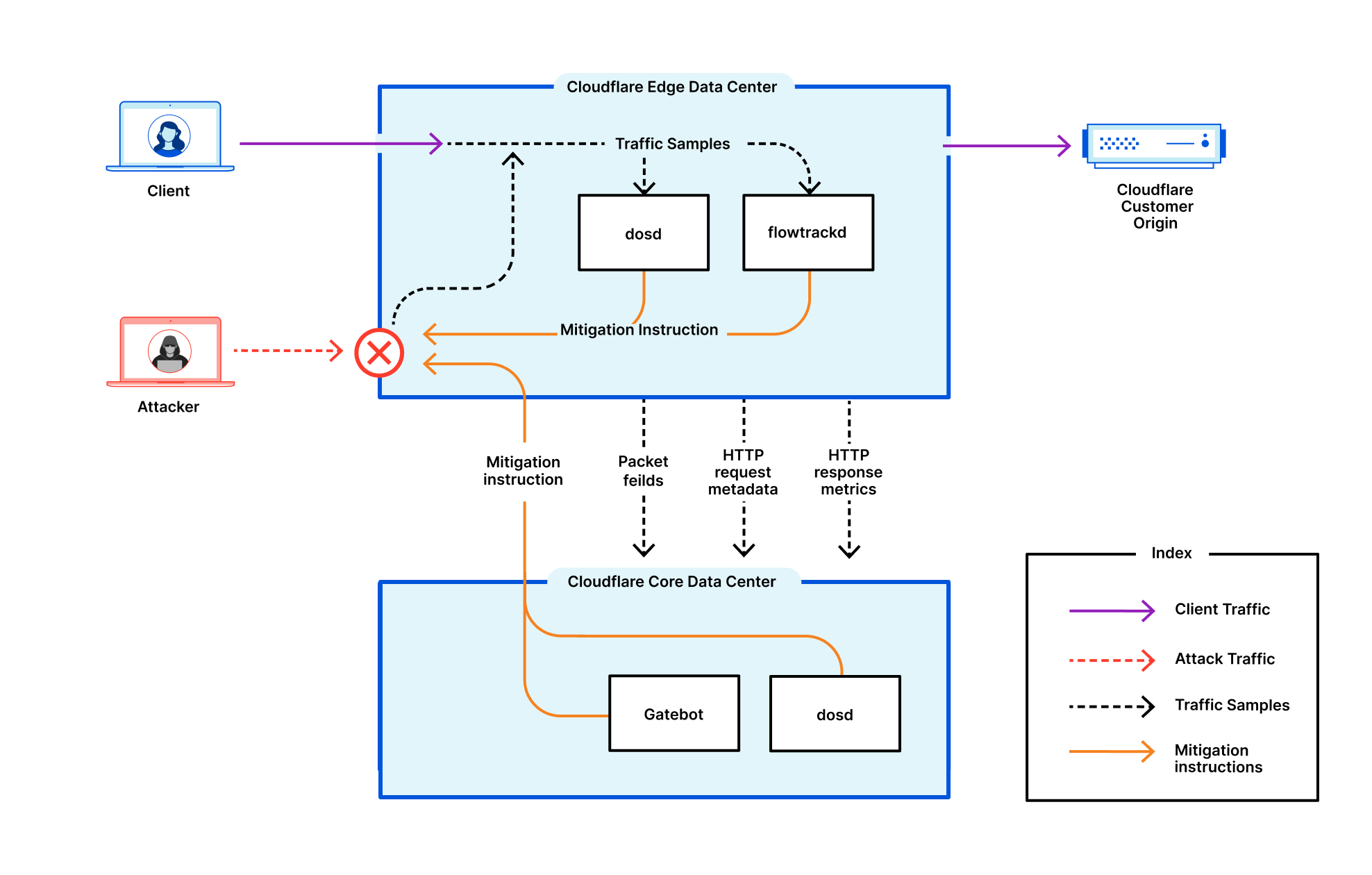
Magic Transit Noise

ドライバーのセキュリティ チェックリスト Windows Drivers Microsoft Docs
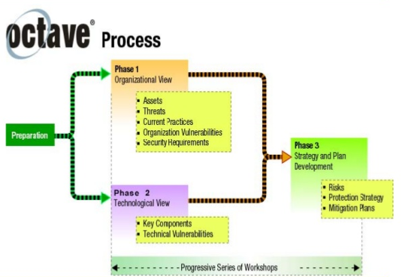
What Is Threat Modeling All You Need To Know Overview

Pdf Security Risk Management In E Commerce Systems A Threat Driven Approach
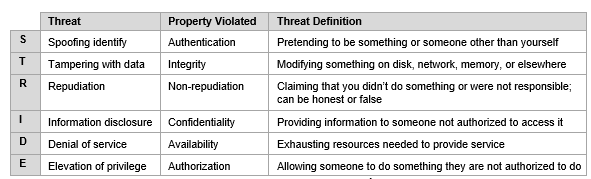
What Is Threat Modeling All You Need To Know Overview